Email Monitoring & Behavioral Analysis
MailX combines proactive monitoring, advanced analysis, and automated remediation to protect organizations from email-based threats.
Real-Time Threat
Detection
Comprehensive
Analysis
Automated
Remediation
Integration with Threat
Intelligence
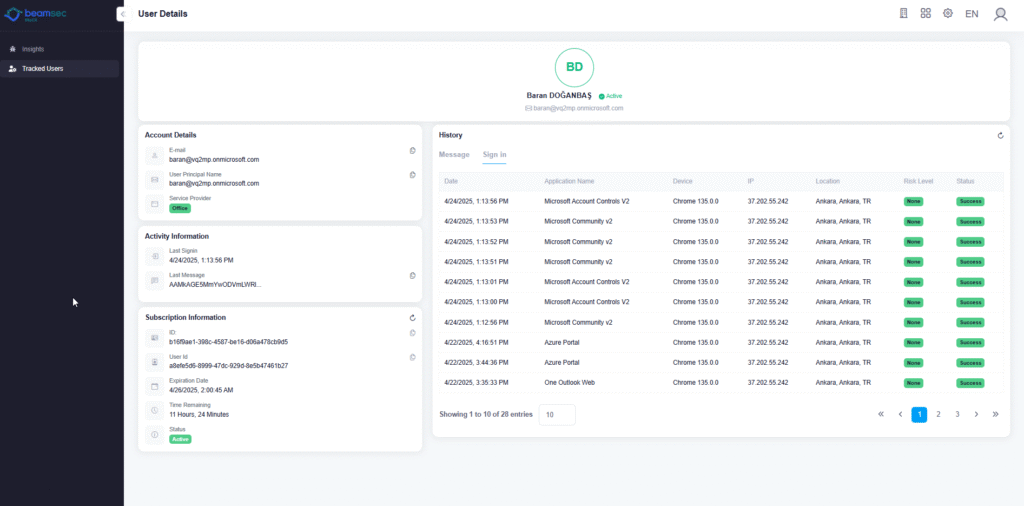
Proactive Monitoring
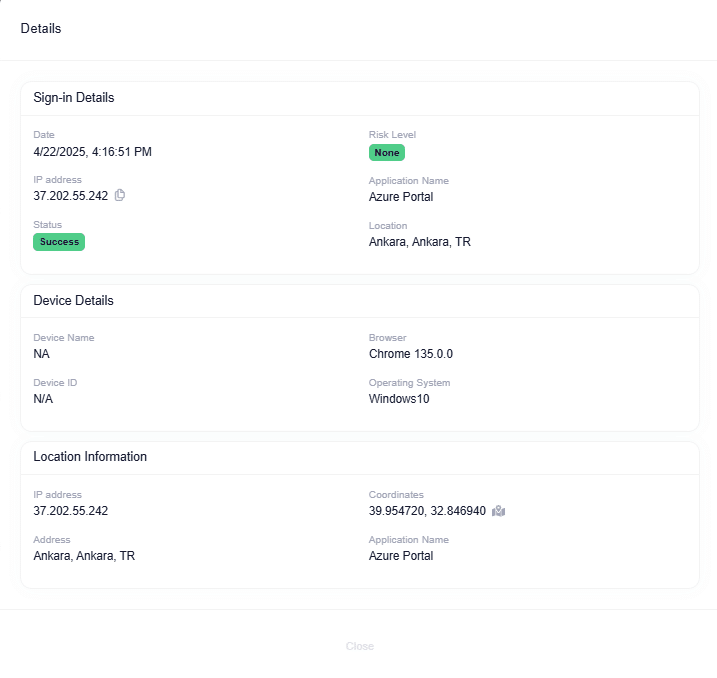
MailX continuously monitors all inbound and outbound email communications to identify potential threats. It conducts comprehensive security checks by analyzing:
- User Information: Verifies sender and recipient details to detect spoofing or impersonation.
- Login Session Details: Tracks login attempts and session activity for anomalies.
- Email Content and Headers: Scans email content, subject lines, and headers for suspicious patterns.
- Embedded Links and Attachments: Examines links and attachments for malicious content (e.g., phishing URLs, malware).
- IP Address Verification: Validates the sender’s IP address to detect spoofing or suspicious origins.
- Sensitive Data Sharing: Identifies emails containing sensitive or confidential information that may be at risk of exposure.
Analysis (Assessment)
MailX uses advanced algorithms and behavioural analysis to detect anomalies that may indicate potential threats. These anomalies include:
- Email Behaviour Anomalies:
- Sudden high-volume email flows from new or unrecognized sources.
- Unusual patterns in email sending or receiving.
- Email Content Anomalies:
- Suspicious or malicious links or attachments.
- Keywords or phrases commonly associated with phishing or scams.
- User Behaviour Anomalies:
- Multiple failed login attempts.
- Excessive password reset requests.
- Activity from dormant or inactive accounts.
- Phishing Indicators:
- Detection of phishing attempts through built-in security algorithms.
When anomalies are detected, MailX immediately sends alerts to administrators or security teams for further investigation.
Remediation
MailX takes corrective actions to mitigate threats and prevent them from causing harm. Its remediation capabilities include:
- Incident Sharing: Automatically shares threat incidents with other threat intelligence tools for coordinated threat prevention and protection.
- Email Filtering:
- Quarantines malicious emails (e.g., malware, ransomware, phishing emails) before they reach the inbox.
- Deletes malicious emails from all users’ inboxes to prevent further exposure.
- URL Blocking: Blocks malicious URLs using DNS protection solutions to prevent users from accessing harmful sites.
- Sender Blacklisting: Blacklists suspicious or malicious senders to prevent future emails from reaching the organization.
- Managed Takedown Services: Triggers managed takedown services to remove malicious content or domains from the internet.