This section is divided into three subsections: “Organization”, “Accounts”, “White Label”
Organization: In this section, you can edit the Name and Title information for the created tenant. Additionally, for the use of two-factor authentication (2FA), the 2FA option must be activated.
The 2FA Authenticator used in the application is based on <style=”color: #00b0f0;”strong>Google’s infrastructure.
Accounts: This section is used to assign permissions to users who will have administrative privileges within the application. These users differ from those added in the Users section, as they are granted higher-level management rights.
How to Add Accounts
Essential information before adding users;
Regular users are manually created within the application.
There are three types of account integrations available: Regular, LDAP, and Azure AD. Additionally, to generate an API token, you can select the API option on the same screen and create a key.
The LDAP and Azure AD account types should be selected for users that are imported from these respective sources.
The application comes with three predefined roles. Based on the selected role, users will have the ability to perform specific actions within the application. These roles define the level of access and permissions a user has, ensuring that each user can only perform actions that align with their assigned role.
Role Manager: Users with this role have full authority to perform all actions within the application. These actions include, but are not limited to adding or removing users, launching campaigns, editing users or content, managing settings and configurations. This role grants comprehensive access and control over the application’s functionalities.
Role User: Users with this role have the authority to launch campaigns and manage the Trace application, but they do not have access to the application settings. This role provides operational permissions without administrative access to configuration settings.
Role Auditor: This role is limited to viewing only. Users with this role cannot perform any actions on campaigns or Trace operations; they are restricted to observation without the ability to make changes or execute tasks.
Important Note: In addition to assigning roles to users, the Role API option is used for generating API tokens. This role specifically grants access to create and manage API tokens within the application.
Create Account

The button highlighted in the image is used to create a new user within the application.

After entering the user’s information, selecting the user type, assigning the appropriate role, and choosing the language preference, the registration process is completed by saving the details.
Once the process is completed and the permissions are assigned, the user can log into the application with the role that was designated for them. This ensures that the user can only access and perform actions based on their assigned role.
Customization of Logos

This screen allows for customization of logos within the application. The settings that can be customized include the login screen, main menu, and favicon logos, all of which can be modified from this section.
Add-in
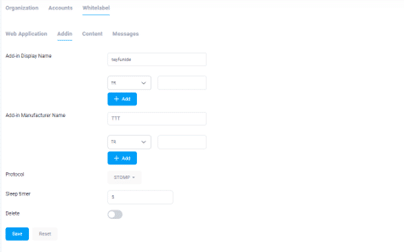
“Add-in“ screen is used for configuring and customizing MSI and XML settings within the application. This section allows for adjustments and personalization of these configurations to meet specific requirements.

As shown in the Outlook screen image, the Display Name is positioned at the top of the add-in, and the Manufacturer Name is displayed directly below it. This layout helps users easily identify the add-in and its developer or provider.
The protocol setting is selected as STOMP. A brief definition is as follows:
STOMP (Simple/Streaming Text Oriented Messaging Protocol) is a simple and widely used protocol that provides an interoperable wire format for messaging communication between clients and message brokers.
Sleep Timer defines the amount of time, in seconds, that the COM add-in waits before initiating a new connection. This timer is used to prevent overloading the server with multiple simultaneous connections by staggering the connection attempts. The default value for Sleep time is set to 5 seconds. However, this setting can be adjusted based on the number of users to optimize performance and prevent server overload.
The delete option is used to determine whether the reported email is moved to the Deleted Items folder in Outlook after the email reporting process is completed. This setting allows you to control whether the reported email is retained or automatically removed from the inbox.

You can customize both Outlook and web applications by uploading your own Add-in logo, allowing for a personalized and branded experience across these platforms.

Logo in educations, emails, and type of content refers to the logo displayed at the end of content such as trainings, tests, and surveys sent to users. Once the content is completed, the custom logo you uploaded will be shown. This allows for consistent branding across all communications and educational materials.

Certificate Customization is used to personalize the certificates sent to users upon successfully completing training campaigns. This feature allows you to add a custom background to the certificate and configure options such as displaying the user’s achievement score. It provides flexibility in designing certificates to reflect your branding and campaign requirements.
Messages
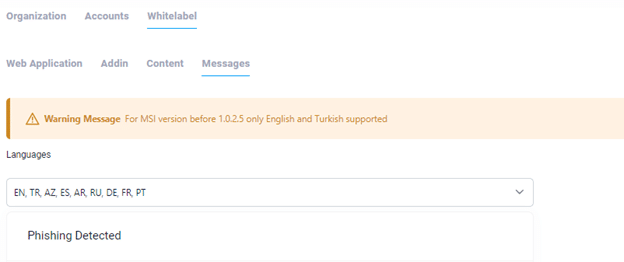
Messages section, customizations are made for the messages that users receive when interacting with the Add-ins. These messages can be customized for various scenarios such as:
– Phishing Detected
– Report Successful
– System Email
– Confirmation
– Error
– Plugin Reset
– Registration
– No Selection
– Disabled
– Duplicate Report
– Reset Confirmation
– Unauthorized
These customizations can be made in the following languages: English, Turkish, Azerbaijani, Spanish, Arabic, Russian, German, French, and Portuguese.
Any changes made for MSI and XML add-ins will be visible to the users interacting with the application.



