What is AD FS?
Active Directory Federation Services (AD FS) is a feature of the Windows Server operating system that extends end-users’ ability to use single sign-on (SSO) to access applications and systems, both on-premises and in the cloud. It uses a claims-based access control authorization model to maintain application security.
Configure Microsoft Active Directory Federation Services Management Console
- In the AD FS Management screen, select “Relying Party Trust” on the left side
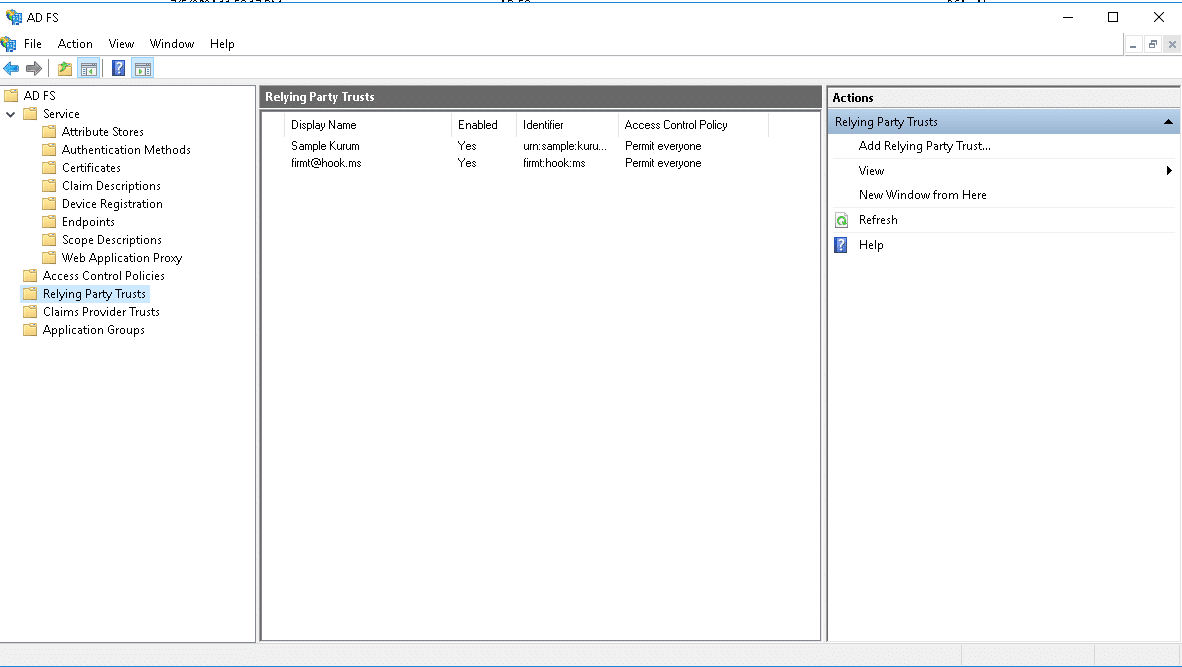
2.Right-click on “Relying Party Trust” and select “Add Relying Party Trust”.

3. In the Add Relying Party Wizard screen, select “Claims Aware” and click the start button.

4. In the Select Data Source screen, check the “Enter data about the relying party manually” option and continue.

5. In the “Specify Display Name” screen that appears, choose a name for the Relying Party Trust you are creating. For example: yourfirm@beamsec.io
6. There are no settings required in the “Configure Certificate” You can continue by clicking the next button without making any changes.
7. In the Configure URL screen, you must select the “Enable Support for the SAML 2.0 WebSSO protocol” Then, you need to add an endpoint for the domain address you use for your application. For this, you need to use the “base domain” address you use in the application.

It should be in the following format: https://yourfirm.com/api/gw/saml/assert
The yourfirm.com in this section is the base domain address you use when accessing the BEAMSEC application.
8. In the Configure Identifiers screen, create an identifier name in the format example:firm:com. The identifier you created will later be used as the Issuer in the BEAMSEC application.
After entering the identifier and clicking the Add button, proceed to the next screen.
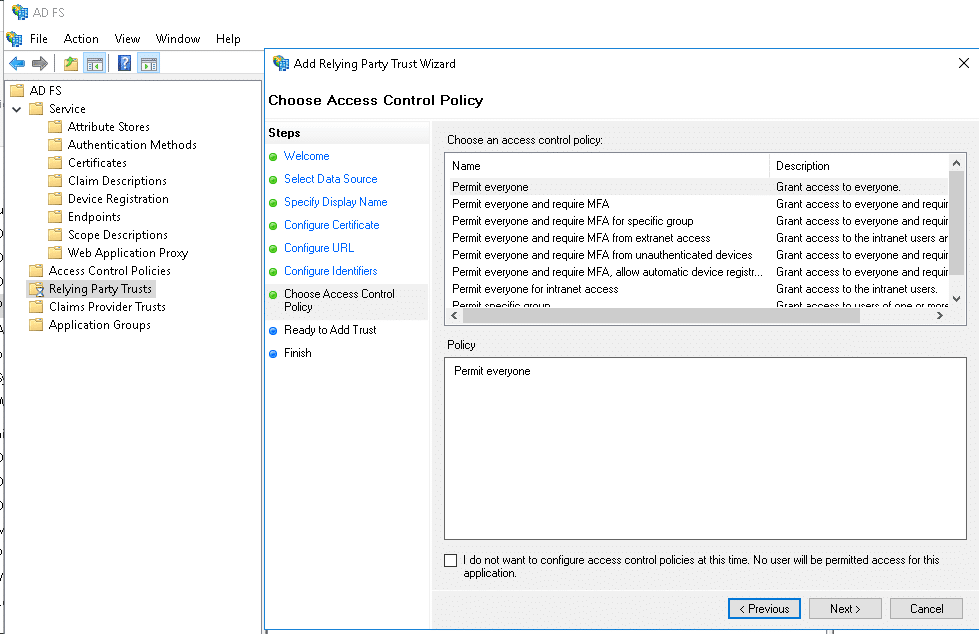
9. Finally, in the “Choose Access Control Policy” screen, select “Permit Everyone” and optionally choose MFA to complete the necessary steps.
Edit Your Issuance Policy
After completing the Relying Party Trust creation process, you need to add an Issuance Policy. This allows users to log in to the application using their email address, group, or custom policies that you have created.
To perform this operation, click on the “Relying Party Trust” you created in the AD FS Management screen and then click on the “Edit Claim Issuance Policy” option on the right side of the screen.
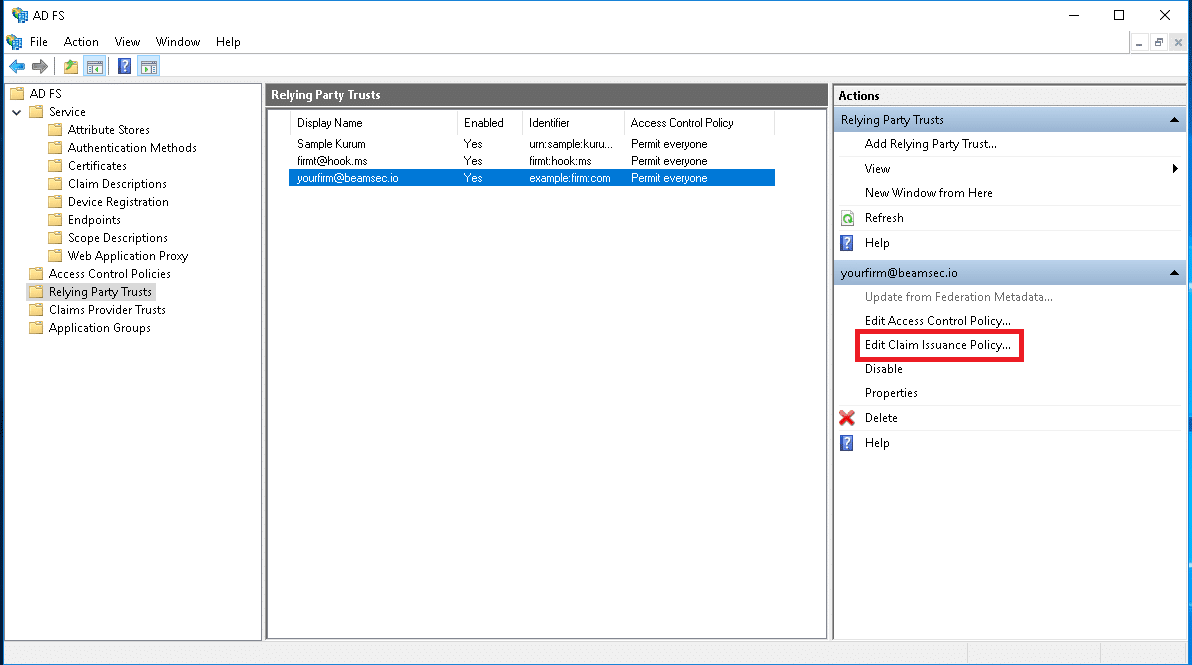
Then, in the “Issuance Transform Rules” window that opens, click “Add Rule” to continue.
- Send LDAP Attributes as Claims

While the “Send LDAP Attributes as Claims” option is selected in the screen that opens, click the next button to continue.

The Attribute Store option should be set to “Active Directory”.
The LDAP attributes should be as follows:
- User-Principal-Name = E-Mail-Adress
The reason for this configuration is that the BEAMSEC application uses the user principal name when synchronizing users from Active Directory.
2. Send Claims Using a Custom Rule

While the “Send Claims Using a Custom Rule” option is selected in the screen that opens, click the next button to continue.
You can complete the process by pasting this value into the Custom Rule field.
c:[Type == “http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname”]
=> issue(store = “Active Directory”, types = (“http://schemas.xmlsoap.org/claims/dn”), query = “;distinguishedName;{0}”, param = c.Value);
3. Send Group Membership as a Claim (Optional)
With this defined policy, if there is a BEAMSEC_ADMIN Organizational Unit in Active Directory, it is required for users within this OU to log in.

While the “Send Group Membership as a Claim” option is selected in the screen that opens, click the next button to continue.

Select BEAMSEC_ADMIN from under User Groups, and complete your settings as shown in the visual.



